Your Guide to FedRAMP Diagrams
Your Guide to FedRAMP Diagrams
2025 Major Update:
- Clarifying authorization boundary and data requirements with latest insights and new examples.
- Updated example Authorization Boundary, Data Flow, and Network diagrams.
- Removed mention of the Joint Authorization Board (JAB)
What is the purpose of this guidance?
Let's take a look
Your organization is looking to sell your service or product and you need to be authorized by a Federal Agency for review and listing on the Federal Risk and Authorization Management Program (FedRAMP) Marketplace. One of the first critical steps is to define your boundary and develop diagrams to be reviewed illustrating that your system and boundary are FedRAMP ready. Government agencies want to know that federal information is properly secured and stored, and that confidentiality, integrity and availability of federal information is maintained. The FedRAMP Project Management Office (PMO), Third-Party Assessment Organizations (3PAO), and agency assessors will be looking for three types of diagrams (minimum). These diagrams include the Authorization Boundary Diagram (ABD), Data Flow Diagram (DFD), and the Network Diagram.
These diagrams should be created as early as possible in the FedRAMP process because they are necessary for developing the System Security Plan (SSP), agency authorization kick-off, and Security Assessment Report (SAR). Remember, the government expects you, as a Cloud Service Provider (CSP), to do your due diligence when illustrating the FedRAMP boundary.
The FedRAMP Authorization Boundary guidance provides expectations for developing, maintaining, and documenting your Cloud Service Offering’s (CSOs) boundary to pursue Agency authorization.
Creating & Storing Diagrams
Due to the potential for Federal Metadata residing in the diagrams, you want to leverage software that is either host-based or FedRAMP authorized at a level that is compatible with your (projected) FedRAMP level (Low, Moderate, or High) during the diagram development process. The Metadata should also be protected once the diagrams are completed by storing them in a secure and encrypted area that also aligns with the specific FedRAMP level you are trying to achieve or within your FedRAMP boundary. FedRAMP authorized tools can be found and accessed via the FedRAMP Marketplace.
Clarity is Key
Diagrams should be clear and concise. Use proper alignment, spacing, and imagery to provide diagrams that are easy to digest. Create each diagram with the same orientation so it is clear to anyone viewing that it is the same system, and transition between diagrams, for comparison is easier. As always, include a legend that clearly identifies the components of your diagrams and use proper labeling within your diagram when necessary. Company-specific icons can usually be downloaded from their website to use in multiple programs. These icons need to be labeled accordingly and/or included in the legend.
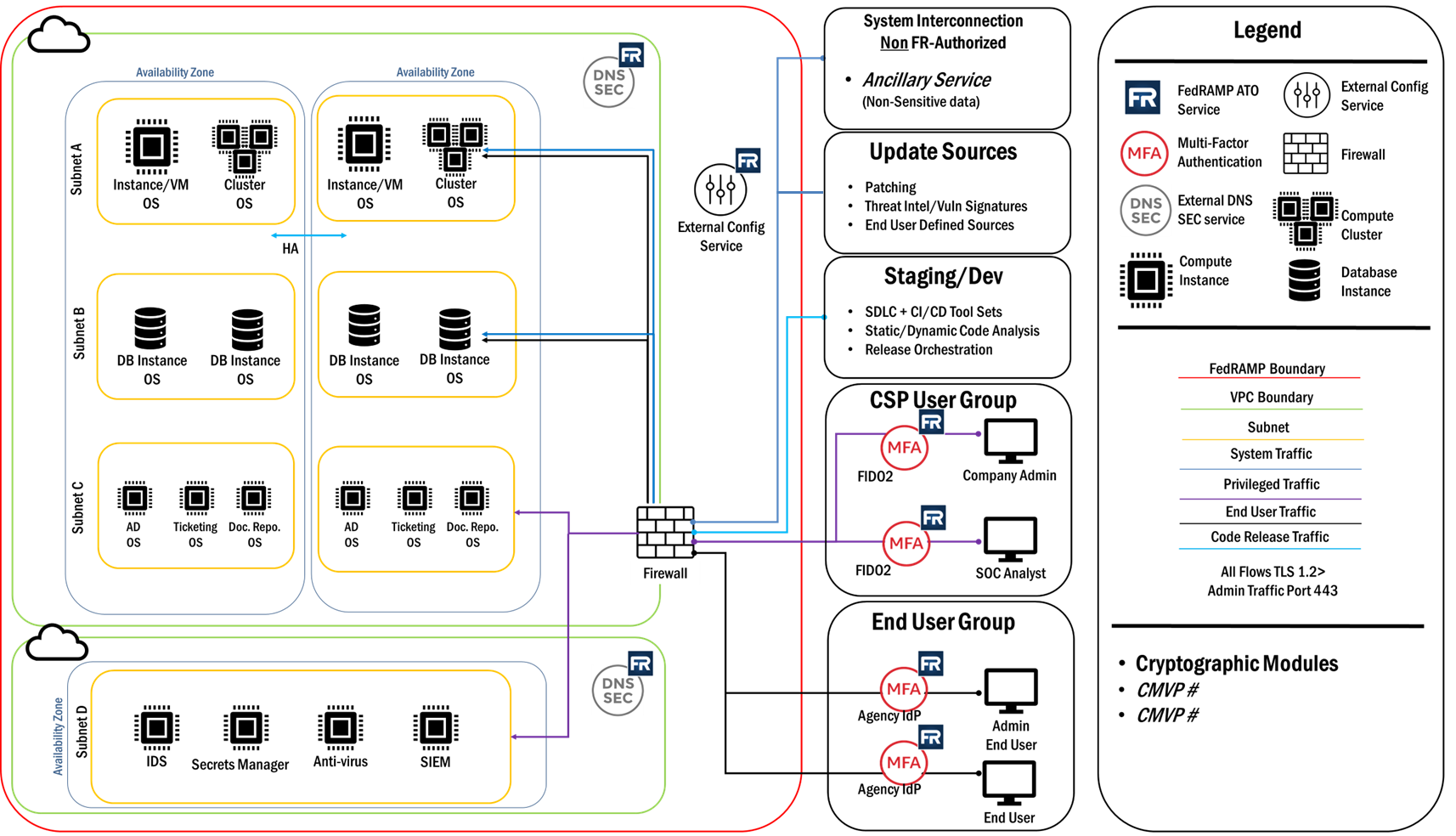
Authorization Boundary Diagram
What is it?
The Authorization Boundary Diagram is a visual representation of the components that make up the authorization boundary by defining the authorization boundary for the CSO. This diagram must illustrate external system/services, system interconnections, every tool, system component and service that is mentioned in the SSP, displaying how your information system connects with external services and systems. The data flow diagram is a living document that is updated and reviewed regularly for accuracy by Agency personnel, Third Party Assessment Organizations (3PAOs) and/or FedRAMP and DISA.
What to include in the Authorization Boundary Diagram:
- Be sure to align with the key concepts and principles outlined by FedRAMP
- Always include a comprehensive legend
- Include a prominent RED border drawn around all system components included in the authorization boundary
- Depict all services leveraged from the underlying Infrastructure as a Service (IaaS) / Platform as a Service (PaaS) / Software as a Service (SaaS) and identify any services that are not FedRAMP authorized
- Depict all ingress / egress points
- Depict how CSP administrators and agency customers access the cloud service and external entities that access the system. If applicable, depict components provided by the CSP, and installed on customer devices, as inside the authorization boundary
- Depict all interconnected systems and external services, including corporate shared services, identify any systems/services that are not FedRAMP authorized
- Depict every tool, service or component mentioned in the SSP narrative and controls, identifying as either external or internal to the boundary. This includes security services used to manage and operate the system (e.g., Security Information and Event Management (SIEM), Vulnerability Scanning, System Health Monitoring, Ticketing)
- Include all components that handle federal data and metadata such as:
- Compute instances (be sure to label as it would appear in the Inventory)
- Database instances (be sure to label as it would appear in the Inventory)
- Authorized 3rd Party Services
- Alternate processing site
- Backups locations
- Compute instances (be sure to label as it would appear in the Inventory)
- Show all connections and components within the boundary and to/from external services as well as the separation and security between the boundary and external services and access
- Show the development/test environment and describe tools at a high level.
- Show your FIPS 140-2/3 validated cryptographic modules in a list view.
- Show update services (e.g., malware signatures and OS updates) outside the boundary
- This includes system interconnections, Application Programming Interfaces (APIs), external cloud services, and Corporate Shared Services
- Be sure to use the legend to differentiate between external services that are FedRAMP-authorized and those that are not. Agency sponsors will need to understand and accept the risk associated with external services that process / store / transmit federal data or sensitive system information (for example: system log files, vulnerability scan data)
- This includes system interconnections, Application Programming Interfaces (APIs), external cloud services, and Corporate Shared Services
Example Authorization Boundary Diagram
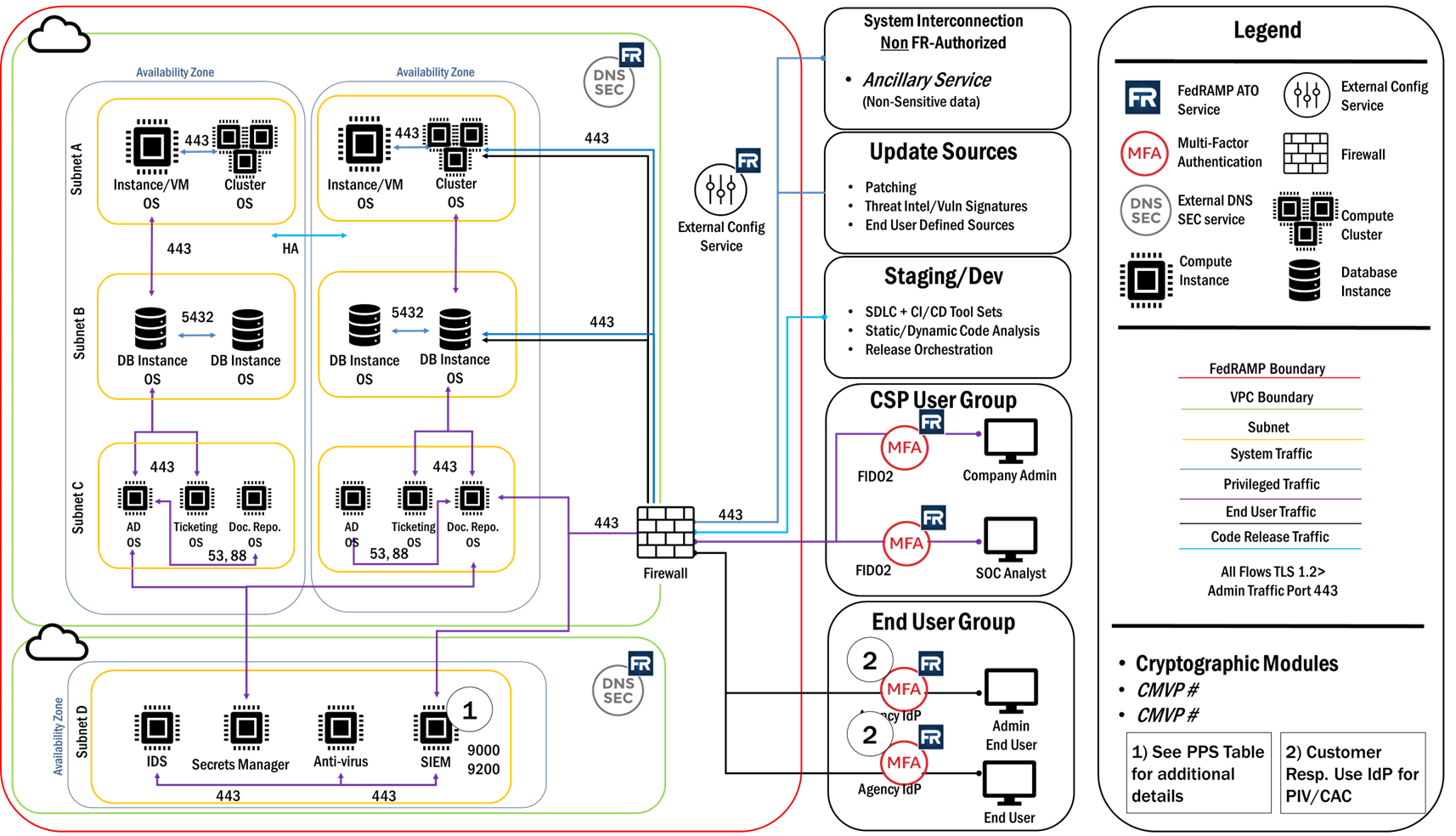
Data Flow Diagram
What is it?
Data flow diagrams illustrate how data moves through the information system as well as the type of encryption while it is in transit or at rest. FedRAMP requires a data flow diagram that should address all components reflected in the ABD, that also delineates how data comes into and out of the authorization boundary, including data transmitted to / from all external systems and services. Data flows should include (but is not limited to) federal customer end-user, administrative and support personnel as well as CSP data flow administrative and support personnel, and system application data flow. The data flow diagram is a living document that is updated and reviewed regularly for accuracy by Agency personnel, Third Party Assessment Organizations (3PAOs) and/or FedRAMP and DISA.
What to include in the Data Flow Diagram:
- Always include a comprehensive legend
- Identify everywhere (internal & external) federal data and metadata at rest and in transit is not protected through encryption. Likewise, identify everywhere data is protected through encryption and whether the encryption is using NSA approved or Federal Information Processing Standards (FIPS)-validated cryptographic modules.
NOTE: FIPS validation applies to cryptographic modules, not protocols (e.g. TLS). The cryptographic module that sets up the TLS tunnel must be FIPS validated
- All data at rest must be protected with NSA approved or FIPS 140-2/-3 validated encryption.
- All data in transit must be protected with NSA approved or FIPS 140-2/-3 validated encryption. This includes federal data and metadata as well as system data (such as audit logs) within the boundary.
NOTE: FIPS 140-2/-3 applies to National Institute of Standards and Technology (NIST) tested and validated cryptographic modules that use approved algorithms.
- All data flow diagrams should address all components reflected in the ABD
- Depict how CSP personnel as well as agency customers access the system.
- Be sure to include authentication methods used and differentiate between privileged and non-privileged access.
- Be sure to include authentication methods used and differentiate between privileged and non-privileged access.
- Depict all ports and protocols for inbound and outbound traffic. (Multiple subcomponent diagrams can be utilized if needed)
Example Data Flow Diagram
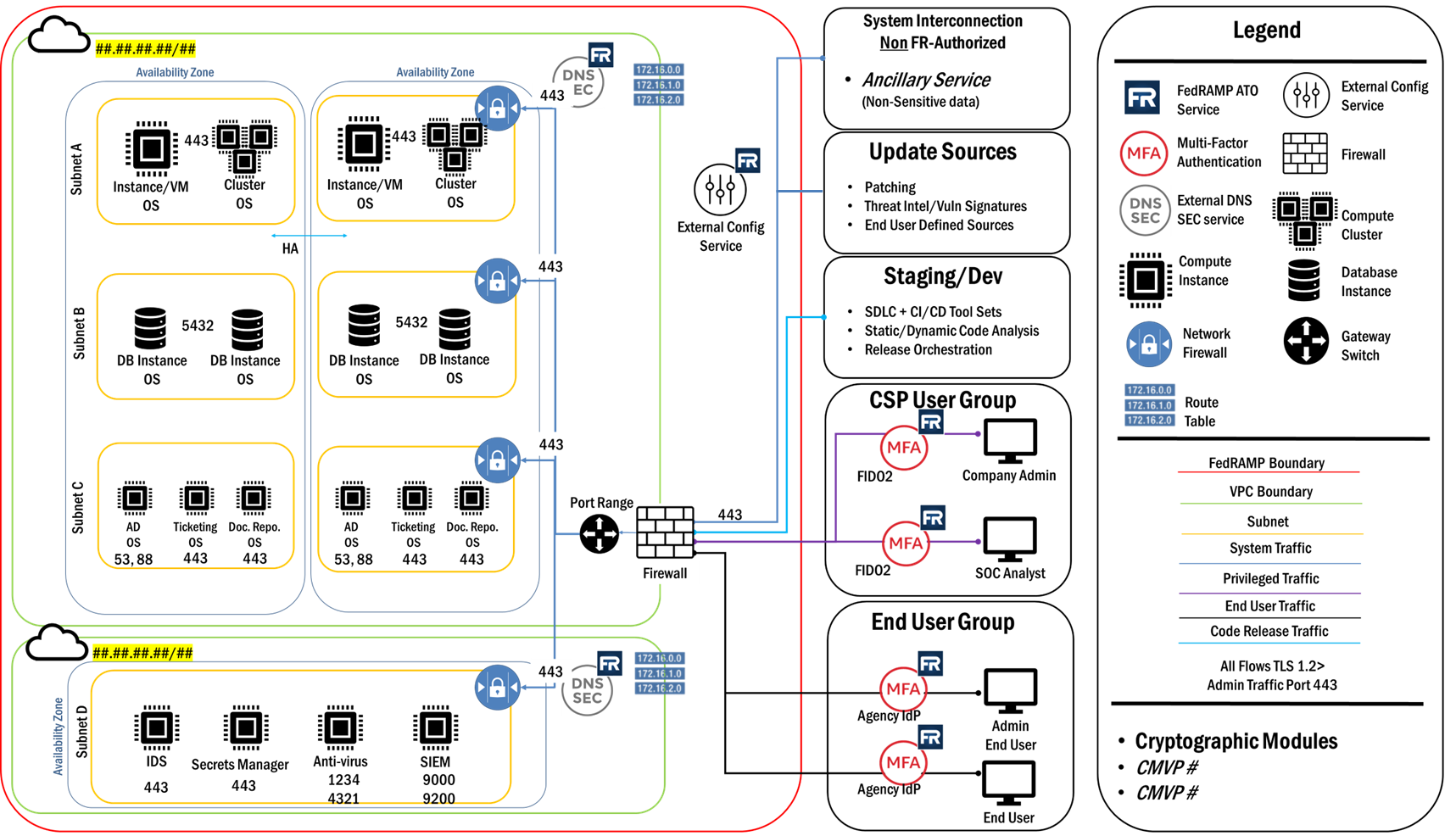
Network Diagram
What is it?
The network diagram should illustrate logical network separation and communication within your network devices such as routers, firewalls, nodes and other hardware (both virtual and physical) located within your environment. The network diagram is a living document that is updated and reviewed regularly for accuracy by Agency personnel, Third Party Assessment Organizations (3PAOs) and/or FedRAMP and DISA.
Network Diagrams should include:
- A legend
- All network devices
- All connections to network devices
- Communications between network devices
- Specific Subnets utilized within the information system
- Depict location of DNS servers:
- Including external authoritative servers used by customers to access the CSO
- Internal recursive servers used to access domains outside the boundary
Example Network Diagram
As Always, InfusionPoints’ FedRAMP Team is here to help......
Whether it’s governing, developing, or deploying your cloud solutions, InfusionPoints provides FedRAMP expertise and workforce so that you can stay focused on your core mission -- by infusing security at every point in the lifecycle of your cloud environment from concept to operations.
For more Information, check out our Cloud & FedRAMP Solution Page HERE
Resources: