Robbinhood: Prince of Ransomware
As some things from our childhood, things aren’t always as they appear.
With what we thought was a vigilante that stole from the rich to give to the poor is now shooting arrows to rob our digital fortresses for self-monetary gain. Already, at least 2 cities have been paralyzed by this dastardly foe known as Robbinhood. Greenville, NC and Baltimore, MD have both been hit with their data held hostage for weeks from over 10,000 city government computers. Just as it’s fifteenth century counterpart, this RobbinHood uses clever strategies to gain access to users; such as Phishing and Social Engineering tactics.
How it gains access to a network is yet to been confirmed, with suggestions it may run from a domain controller or utilize Powershell Empire and PSExec. This ransomware can be described as vanilla as it initiates with the “cmd.exe /c net use * /DELETE /y” command to disconnect all network shares. Next, RobbinHood attempts to read a public RSA encryption key from C:\Windows\Temp|pub.key. If that key is not present, then the ransomware will exit. If it is present, then it will continue the process to encrypt the unsuspecting machine. It then stops 181 Windows services associated with AntiVirus, databases, mail servers, and any other programs that would keep Robbinhood from encrypting. It does this by issuing a simple "sc.exe stop" command.
As part of the evasion process, RobbinHood is covering its tracks by clearing Shadow Volume Copies, event logs and disabling the Windows Automatic repair. When encrypting files, an AES key is created for each file which is then encrypted along with the file and a public RSA encryption key. Each encrypted file is then renamed with "Encrypted_{randomstring}.enc_robbinhood”.
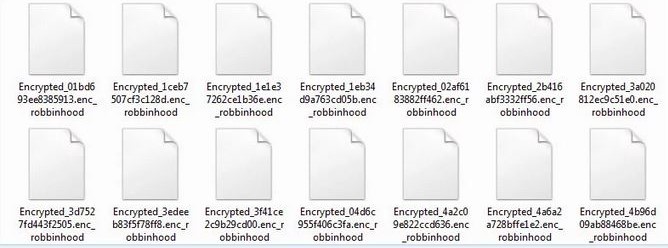
RobbinHood will also skip files that are essential for windows to operate because how else would you see its playful banter.
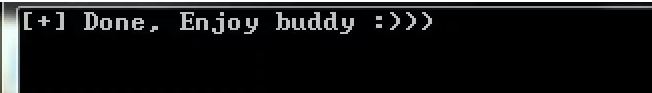
The ransomware will create several log files under the C:\Windows\Temp folder. It's currently unknown what each log file is, other than the rf_s file. That log is used to record the creation of ransom notes in each folder. Once the encryption process has been completed, all associated logs are removed from the system. During the encryption process, four different ransom notes are created: _Decrypt_fiels.html, _Decryption_ReadMe.html, _Help_Help_Help.html, and _Help_Important.html.
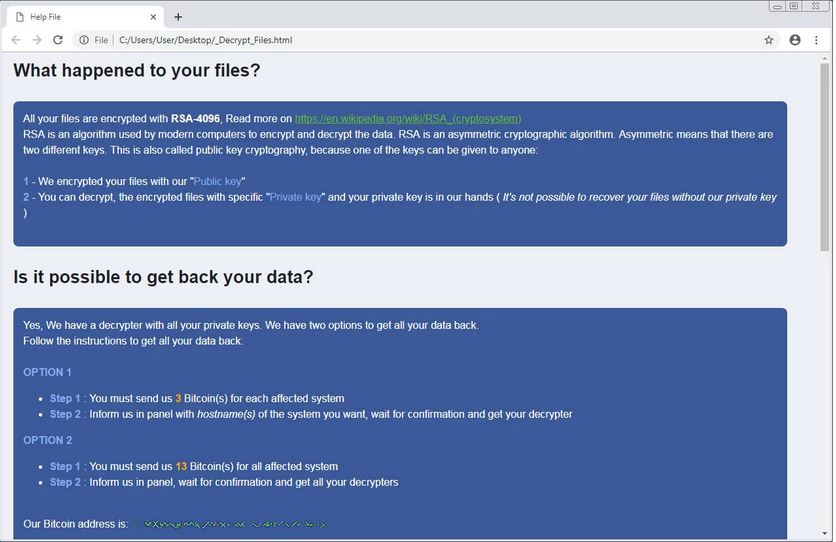
These ransom notes left by our digital man in tights, RobbinHood, provides insight on what’s recently transpired on the victim’s files along with a bitcoin address where they would like their deposit. The payments are kindly accepted as either 3 bitcoins per workstation or 13 bitcoins as a lump sum for all devices, which would be over $103,000. As if this was not enough, you can expect the price to increase $10,000 a day after the fourth day of non-payment.
How can you prevent your fortress from being taken over and held for ransom? Especially now that bad actors, such as Robbinhood, are deploying these ransomware attacks more evasively by becoming less sophisticated. Utilizing built-in administrative tools such as the aforementioned powershell, psexec, and other everyday enterprise utilities. The most important thing you can do is have a reliable backup of your data. Backups stored at a cold site, where they are isolated from the infection, would be ideal. Ransomware itself is not spread by spam. It is possible that it is being installed by Trojans that are training users to properly identify malicious spam and not opening attachments without confirming who and why they are sent is vital!
Don’t wait until a critical event occurs to protect your environment, allow InfusionPoints to monitor your environment 24/7/365 to catch the events before they happen.
If you do wait and an event happens, we at InfusionPoints pride ourselves in handling critical situations such as these with the same finesse and secrecy as Yahya, or Little John. With our 24/7/365 VNSOC, expert analysts and engineers are ready to guide you from contamination to remediation. We want to help you reduce total cost and increase your overall digital posture. We keep an eye on your environment allowing you to focus on the things that are most prevalent for your kingdom.
Written by:
Steffon Lassman
Anthony Guynes


