InfusionPoints XccelerATOr Logging Architecture
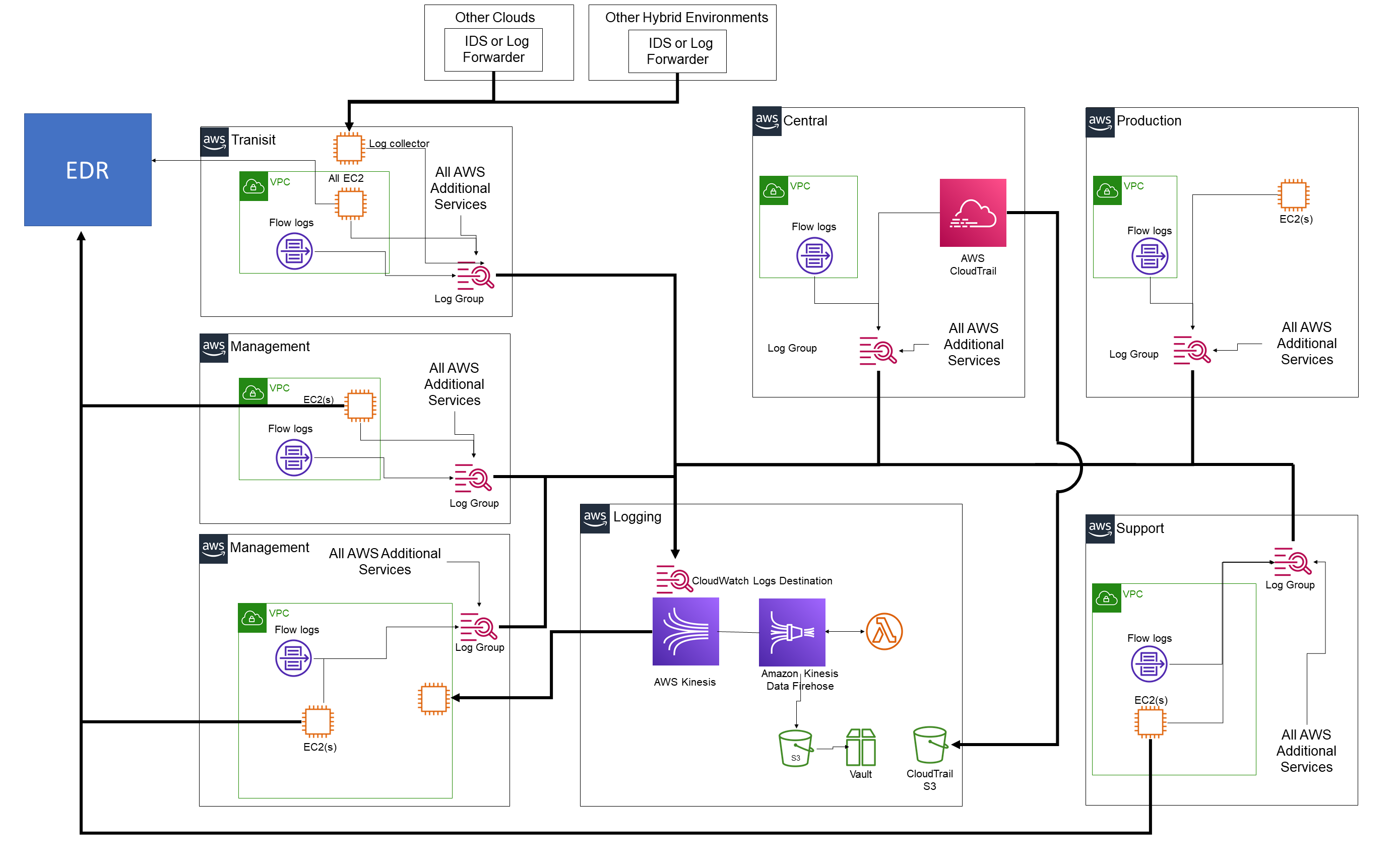
InfusionPoints' XccelerATOr Infrastructure as code (IAC) leverages a set of detection mechanisms in each account. This base set of mechanisms is aimed at detecting a wide range of actions on all resources in each account. InfusionPoints' XccelerATOr IAC has a comprehensive detective capability and leverages the following AWS services:
- AWS CloudTrail provides event history of AWS account activity, including actions taken through the AWS Management Console, AWS SDKs, command line tools, and other AWS services.
- Amazon GuardDuty provides threat detection services that continuously monitors for malicious activity and unauthorized behavior to protect each account.
- AWS CloudWatch provides distributive log collection from all of the AWS accounts, systems, applications, and AWS services.
- AWS CloudWatch Unified Log Agent provides EC2 instances and application-based logging that does not originate from AWS services, logs and are sent to Amazon CloudWatch Logs. AWS CloudWatch Unified Log Agent collects the logs from each operating system and application that is running, and automatically sends them to the central logging AWS Account via AWS CloudWatch Log groups.
- AWS Kinesis Streams collect the logs from CloudWatch Log group (All logs are encrypted leveraging AWS KMS), the logs are processed in real-time, and sent to Kinesis Streams in the centralized AWS logging account.
- AWS Kinesis Firehouse and Lambda formats and filters the logs and sends the logs for storage and archives in AWS S3.
- VPC Flow Logs capture information about the IP traffic going to and from network interfaces to provide valuable insight into connectivity history, and trigger automated actions based on anomalous behavior.
- AWS multi-account approach, InfusionPoints XccelerATOr IAC implements many core AWS services in each account.
- The Logs are picked up by our SEIM and monitored, analyzed, and acted on appropriately.
In addition, XccelerATOr configured infrastructure can ingest logs from additional cloud infrastructures or hybrid environments as well. XccelerATOr logging configuration can ingest logs from intrusion detection systems or log forwarders, and process the log the same way as logs that are generated in AWS
The Virtual Network and Security Operations Center (VNSOC) team rely on the collection of logs and the use of search tools to discover potential events of interest, which might indicate unauthorized activity or unintentional change. However, simply analyzing collected data and manually processing information is insufficient to keep up with the volume of information flowing from the InfusionPoints XccelerATOr architecture. Analysis and reporting alone do not facilitate the assignment of the right resources to work an event in a timely fashion.
The VNSOC team is deeply integrated with the flow of security events and findings and leverages several notifications and workflow systems such as a ticketing system as well as a security information and event management (SIEM) system. This takes the workflow out of email and static reports, and allows the team to route, escalate, and manage events or findings.


