Exploring the World of DISA STIGS: An Introduction
The world of cybersecurity can manifest complex problems, obfuscated puzzles, and skilled bad actors that you will inevitably encounter during your journey within the industry. Luckily, security professionals have a plethora of tools at our disposal and Defense Information Systems Agency (DISA) Security Technical Implementation Guide’s (STIG), are among the most useful. DISA STIG’s can transform how you approach security and assist you with your system hardening endeavors. Let’s take a quick look at where these STIG’s come from, what they are, and how to use them.
Where do STIG’s Come From?
Under the umbrella of the Department of Defense (DoD) lies DISA, which houses the Field Security Office (FSO) of the Information Assurance Support Environment (IASE) for the creation of each STIG (there’s your concentrated dose of acronyms for the day), DISA supports the IT and communications efforts for all individuals working for the DoD. Just as our technology, as well as our adversaries, are evolving and ever changing, so are DISA STIG’s. Although not policy mandated, implementing configurations outlined in a STIG means taking a step towards mitigating a risk. Conversely, not implementing a configuration in accordance with the STIG insinuates an acceptance of the risk. STIG’s are updated and released every 90 days through the Public DoD Cyber Exchange! This helps ensure that companies can effectively maintain secure hardware and software. You can also search for and review up-to-date STIG’s via the STIG Viewer, which is a more user-friendly approach to viewing STIG requirements.
What Are STIG’s and How Do We Use Them?
STIG’s provide a structured guideline that describe how organizations should build and maintain vendor specific systems and software, securely. There are hundreds of STIG’s at our disposal with each piece of technology having a STIG allocated to them, from Apple iOS to VMware’s ESXi.
So, what is a Security Technical Implementation Guide (STIG)? A STIG is a configuration standard for adhering to security requirements for a given vender-specific component, such as Windows 10. The Microsoft Windows 10 STIG, as seen on STIG Viewer will be used for this example, and is structured such as this:
An Overview
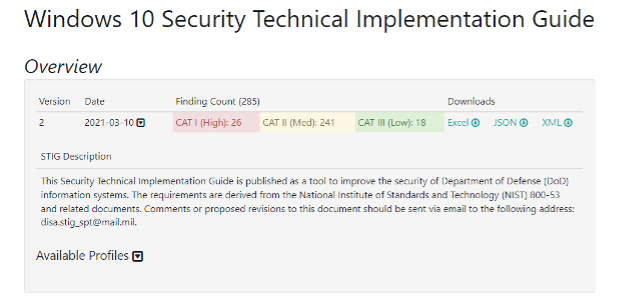
This acts as a summary of the STIG, which includes the version, date, finding count (broken down into severity CAT I High, CAT II Medium, and CAT III Low), and a STIG description. There are options to download the Windows 10 STIG via Excel, JSON, and XML files within this section as well. Mission Assurance Category (MAC) levels are tied to each finding and gauge the level of protection needed, which can be reviewed below:
- MAC I – The system handles information that is critical to operational readiness, or mission effectiveness. The loss of availability, or integrity, of MAC I systems is considered unacceptable.
- MAC II – The system that handles the support for any deployed or contingency forces. The loss of a MAC II system can only be tolerated for a short margin of time.
- MAC III – The system that handles information that is prudent for the day-to-day operations. Any MAC III loss can be tolerated without largely impacting mission effectiveness, or operational readiness.
A Collection of Findings
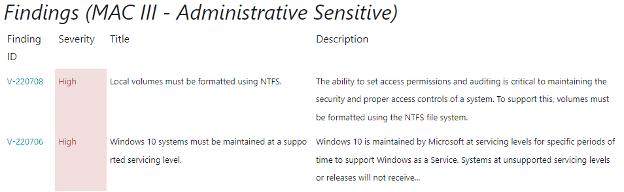
These findings represent the requirements necessary to improve the security for information systems and software alike. Something of note is these requirements are closely tied to the controls detailed in the NIST 800-53 documents. In this section you can review information such as the Finding ID, severity category, finding title, and a description of the finding.
The Findings
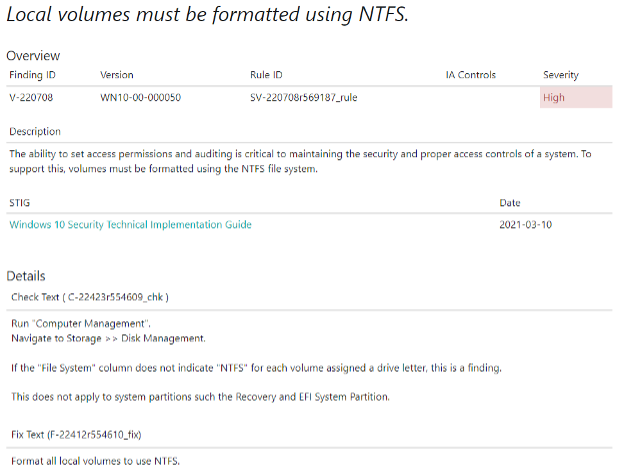
By clicking on the “Finding ID”, you can view more details regarding a specific finding. Here you can learn about the methods used to check the component for proper configurations, in addition to the steps necessary to secure a given component.
All this information combined goes into creating a strong foundation that, if properly used, an organization can be afforded some piece-of-mind regarding their security.
AWS Services leveraged
- Amazon VPC
- Amazon EC2
- Amazon EBS
- AWS Systems Manager
- AWS Inspector
- AWS Guard Duty
Is There Anything Else?
Yes! The world of DISA’s STIG’s is vast and ever evolving. These STIG’s are effective at hardening information systems and software alike. However, they can also be used to assist with any compliance needs you may have, like FedRAMP or NIST 800-53, due to where these requirements are derived from. In the event a STIG may not be available, referring to the Security Requirement Guide (SRG), in addition to the NSA guide is considered best practice. Be on the lookout for our next blog on Security Requirement Guides (SRGs)!
Curious about STIG’s? Come ask us about how we can help build, manage, and defend your architecture with the assistance of STIG’s!


