DISA Releases Rev 5 Cloud Computing Security Requirements Guide
DISA Releases Rev 5 Cloud Computing Security Requirements Guide
Updated August 18, 2024: Latest DoD SSP Addendum Insights for IL4/5/6. See the impact in 'What Changed?' below.
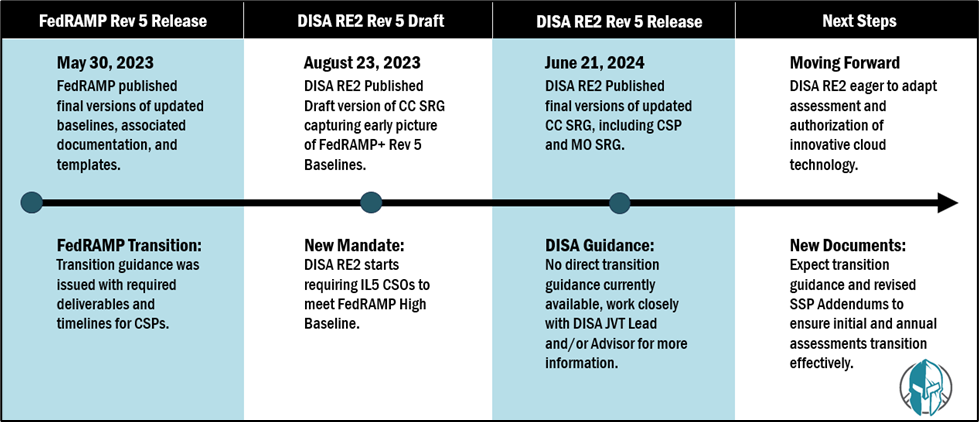
Following the release of NIST Special Publication 800-53, Revision 5, the DISA Cloud Assessment Division (RE2) has released new Cloud Service Provider (CSP) and Mission Owner (MO) Security Requirements Guides. CSPs targeting a DoD Provisional Authorization (PA) or looking to recertify their existing DoD PA, will need to consider the impact to their security implementations, processes, and documentation, as well as their overall compliance program.
While a revision history was provided, it does not provide details on the major changes in the latest version of the Cloud Computing SRG which will be broken down in this blog. With the new Cloud Computing Security Requirements Guide (CC SRG), DISA has provided improved clarity on guidance and roles and responsibilities of various stakeholders. The structure has undergone significant changes as DISA has worked to reduce complexity and enhance understanding. By eliminating redundancy and establishing overarching directives early on, such as DoD Issuances (DoDIs), STIGs, and SRGs, readers will notice easier navigation.
A brief timeline is summarized below in figure one:
What Changed?
This edition of the CC SRG marks the shift from NIST 800-53 Rev 4 to Rev 5 and incorporates the requirements outlined in CNSSP-32 for National Security Systems. It exclusively addresses the Rev 5 requirements, without any content on Rev 4. The CC SRG is now divided into two sections, one for Mission Owners and another for CSPs. Due to the withdrawal of certain controls and the consolidation of other controls in FedRAMP Rev 5 baselines, DISA has accounted for this by reducing FedRAMP+ Additions/Adjustments which reduces total controls for IL4/5/6, check the Appendix below for a breakdown. Notably, the FedRAMP High Controls Baseline path is now firmly required for all IL5 CSOs. This has been a recent requirement from DISA, but is now established per SRG. This does not necessarily require a CSO to be listed in the FedRAMP Marketplace as FedRAMP authorized at the High baseline prior to submitting for IL5, but you must be able to demonstrate FedRAMP High Baseline controls compliance with additional IL5 controls during your IL5 audit. Essentially there is no longer a path to IL5 leveraging the FedRAMP Moderate Baseline.
As of July 19, 2024, DISA has released the latest DoD SSP Addendum controls in Excel format. This is a positive development for digital authorization packages as it enables easier indexing for controls outside of a Word document. However, the latest Addendum captures all controls within the FedRAMP+ DoD baselines without indicating which controls are additional or changed for DoD, requiring CSPs to put in additional upfront work to transition from standard Word formats to Excel in Rev 5. There is also a new indication for National Security Systems (NSS) vs Non-NSS with major control variations. These changes have the potential for wide reaching impact on CSPs and Mission Owners including user access, phishing resistant MFA, zero-trust, and PII/PHI considerations.
Control Change Overview
Considering the withdrawal and consolidation of certain controls in NIST 800-53 Rev 5, the new FedRAMP High and Moderate baselines have fewer controls. DISA has addressed this by removing previous controls and re-assigning those not in the FedRAMP baselines for IL4/5/6. With the official release of the DoD SSP Addendum for IL4/5/6, specific control assignments and requirements are now available to CSPs. See a comprehensive breakdown in the Appendix: Control Considerations.
All controls from the FedRAMP+ Rev 4 baselines have been removed and replaced with an entirely new list of FedRAMP+ Rev 5 controls, provided in the Appendix below. CSPs will need to carefully review which controls are no longer in scope and which have been consolidated in the FedRAMP Rev 5 baselines to avoid risks to DoD PA. IL5 CSOs deemed National Security Systems (NSS), identified in the system’s CNSSI 1253 designation, have more stringent control additions and adjustments.
The SRG no longer states that “CSPs may offer equivalent 3PAO assessed controls or mitigations which will be considered on a case-by-case basis,” making it critical to implement all required controls to avoid potential risk findings. It's important to note that Mission Owner (MO) SLA controls are selected by the MO and are not included in the assessment toward a DoD PA.
- FedRAMP+ IL4 Baseline: Removed 38 controls; Added 22 controls
- FedRAMP+ IL5 Baseline: Removed 47 controls; Added 21 controls
- FedRAMP+ IL5 NSS Baseline: Removed 47 controls; Added 178 controls
- FedRAMP+ IL6 NSS Baseline: Removed 47 controls; Added 209 controls
- FedRAMP+ IL4/5/6 Baseline(s): Maintained 10 GR controls*
- FedRAMP+ Mission Owner SLA: Maintained 13 MO SLA controls
- IL4: Maintained selection of 9 controls
- IL5: Expanded selection to 13 controls
- IL6: Expanded selection to 13 controls
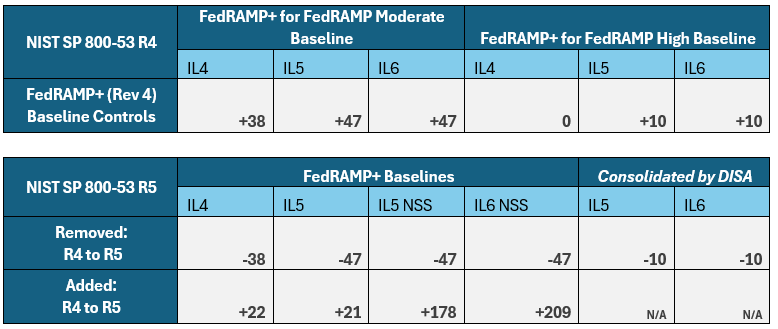
Figure 3. FedRAMP+ Control Change Overview.
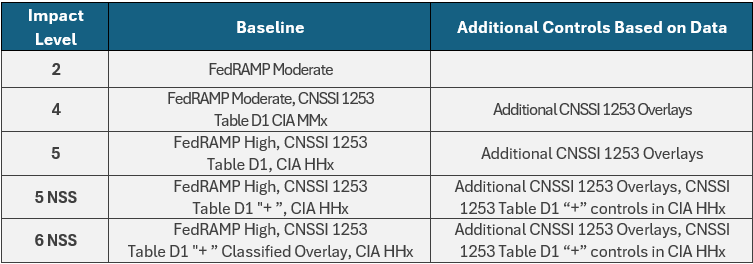
Figure 4. Minimum DoD PA Assessment Controls.
Boundary Cloud Access Points:
The Boundary Cloud Access Point (BCAP) remains a firm requirement for IL4/5/6 Mission workloads connecting to NIPRNet or SIPRNet, unless approved and waived by DoD CIO for IL4/5. The latest SRG clarifies these requirements for CSPs and MOs and consolidates topics such as meet-me-points under existing headings and subheadings.
Virtual and Physical Separation Requirements:
Data and workload separation requirements have also seen a revision, with this section clarified as “Impact Level Separation Requirements” vs the former “Cloud Deployment Model Considerations/Separation Requirements.” Importantly, the physical separation compute and storage for isolated IL5 workloads in IL4 authorized CSOs is no longer documented as acceptable, which was previously documented under “Impact Level 5 Separation in an Impact Level 4 CSO.” Firm requirements for physical separation from non-DoD/non-federal government tenants at IL5, and strong virtual isolation at IL4, remains in-scope in the latest SRG.
Identity and Access Management:
In the latest Cloud Computing SRG, Section 5.4.1 outlines best practices for identity credentials at different Impact Levels. For IL4, it is preferred to use hardware token technology combined with multifactor authentication, a one-time password, or a PKI certificate, adhering to DoDI 8520.03 Credential Strength D. However, at a minimum, identity credentials should use a multi[factor-]token solution or a multifactor, one-time password solution, corresponding to DoDI 8520.03 Credential Strength C.
For IL5, the standard is higher, requiring identity credentials to use hardware token technology that implements a multifactor one-time password or a PKI certificate solution, specifically DoDI 8520.03 Credential Strength D. While this newly released SRG appears to accept MFA OTP or PKI for CSP privileged credentials at High IL5, the control IA-2, and its enhancements, emphasize zero-trust and phishing-resistant MFA in the FedRAMP Baseline. It remains to be seen how DISA RE2 will handle phishing resistant MFA for Provisional Authorizations (PAs), but it appears that Credential Strength D OTP may still be acceptable if compliant hardware tokens are leveraged.
The new CSP SRG also allows for Just in Time (JIT) or Just Enough Access (JEA) for CSP personnel, which lowers the security investigation requirement per Office of Personnel Management (OPM) guidance for technical supervising and subordinate administrators with access to sensitive data.
Supply Chain Risk Management:
The latest update revises Section 5.12, focusing on Supply Chain Risk Management. Although DISA has already enforced a Supply Chain Risk Management Plan (SRCMP) through the selected control SA-12, the addition of the SR control family indicates a likely increase in scrutiny. CSPs should proactively ensure their supply chain posture is up-to-date with robust controls and measures to detect and prevent counterfeit components and enforce secure software development practices. This includes implementing new training programs to address emerging threats and vulnerabilities. For more details on improving supply chain security, refer to our previous blog on Secure Software Development Framework and its impact for more information.
Personally Identifiable Information (PII)/Protected Health Information (PHI):
The latest update to the Cloud Computing SRG has removed Section 5.1.5, and tables containing parameter values, which previously addressed PII and PHI in the cloud. While privacy concerns are now more prominently featured in the NIST 800-53 Rev 5 and the FedRAMP Baseline, explicit mentions of PII/PHI and Privacy overlays have been omitted from both the CSP SRG and Mission Owner SRG.
This change does not imply that privacy overlays are not scrutinized in DoD, as DISA notes, “overlay values take precedence,” on the contrary, Mission Owners, particularly those managing IL4/5 systems, continue to prioritize privacy as a standard where PII/PHI is processed, stored, or transmitted. CSPs will likely be required to incorporate additional controls to meet overlay requirements per Mission Owner directive for Privacy, CNSSI 1253, and DoD RMF. Mission Owners and CSPs must ensure that privacy controls are adequately addressed to protect sensitive information in the cloud. It appears this streamlined approach aims to simplify the document while maintaining robust privacy and security standards established in Rev 5 baselines.
Mission Owner SRG:
The Cloud Computing Mission Owner Security Requirements Guide (SRG) outlines technical security policies for DoD Mission Owners' cloud environments, complementing the Cloud Service Provider SRG. It is directed at program managers within DoD components who create cloud service instances using CSP offerings that have a DoD Provisional Authorization (PA). While missions above Secret are not covered and must follow existing DoD policies, the SRG emphasizes the importance of understanding the division of security responsibilities between the organization and CSPs. Security duties vary depending on the cloud service type (IaaS/PaaS/SaaS) and specific CSP offerings, making it crucial for Mission Owners to manage these divisions effectively, a common paint point on both CSPs and MOs.
What’s Next?
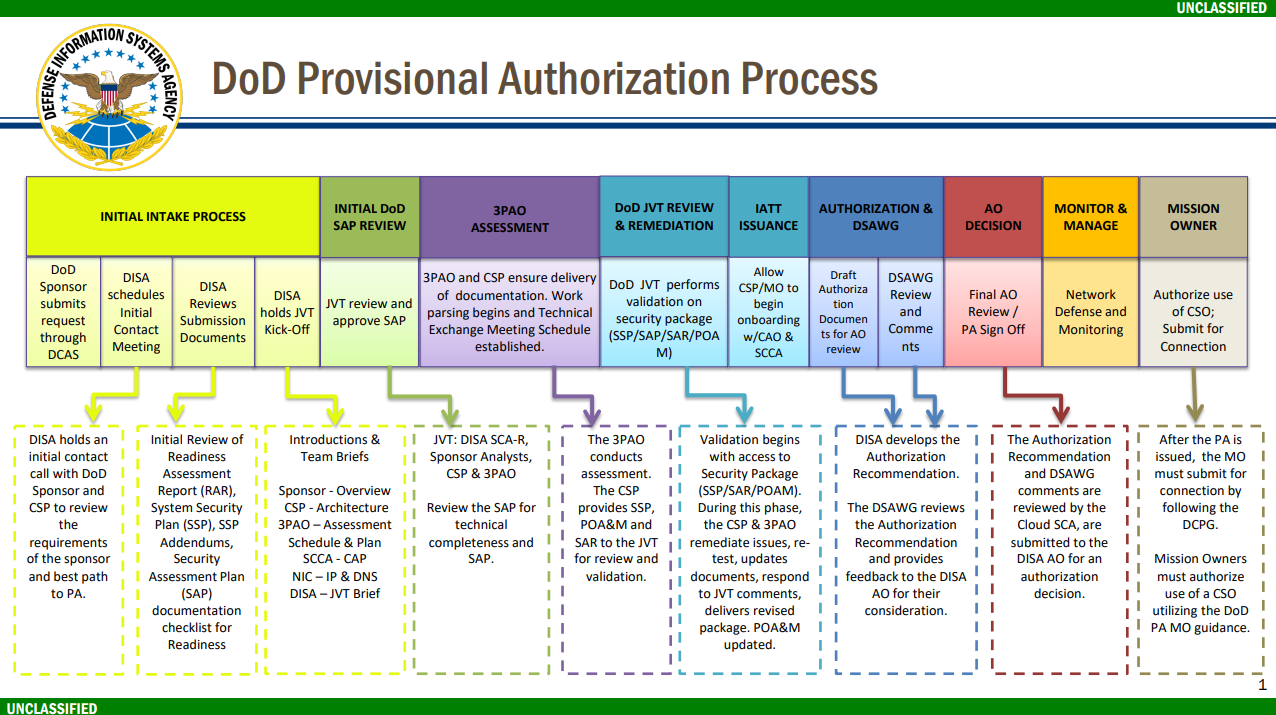
DISA is now at Rev 5! Readers can use these SRGs as a comprehensive hub, supported by extensive documentation like the DISN Connection Process Guide, DoDI, and STIGs/SRGs, which streamlines the review and consideration of cloud security requirements without the need for redundant call-outs to referenced documents. Additionally, the breakout of documents for CSPs and MOs provides greater accessibility to stakeholders on both sides of the engagement and consolidated control additions/adjustments provide more consistency with FedRAMP Rev 5 Baselines, while still allowing Mission Owners’ discretion in mandating control overlays. The pivot to Rev 5 indicates similar changes and timeline expectations for transition. It’s important to work closely with your Agency, DISA JVT Lead, or Advisor to stay up to date on expectations for 3PAO assessment.
Looking forward, the DoD recognizes that innovative approaches in cloud computing environments may replace some traditional defense-in-depth mitigations designed for physical networks and servers. DoD is keen on evaluating equivalent alternative measures, which DISA will assess on a case-by-case basis. This forward-thinking approach demonstrates commitment to evolving and adapting security measures to meet the dynamic innovations in cloud computing.
No official transition guidance has been issued by DISA RE2 at the time of this blog update, August 18, 2024. Continue to check back here for deeper dives into the impact as we work closely with DISA RE2 to obtain updates.
Contact InfusionPoints for assistance with understanding how the DoD’s shift to Rev 5 impacts your mission or CSO.
Contact Us
Appendix: Control Considerations
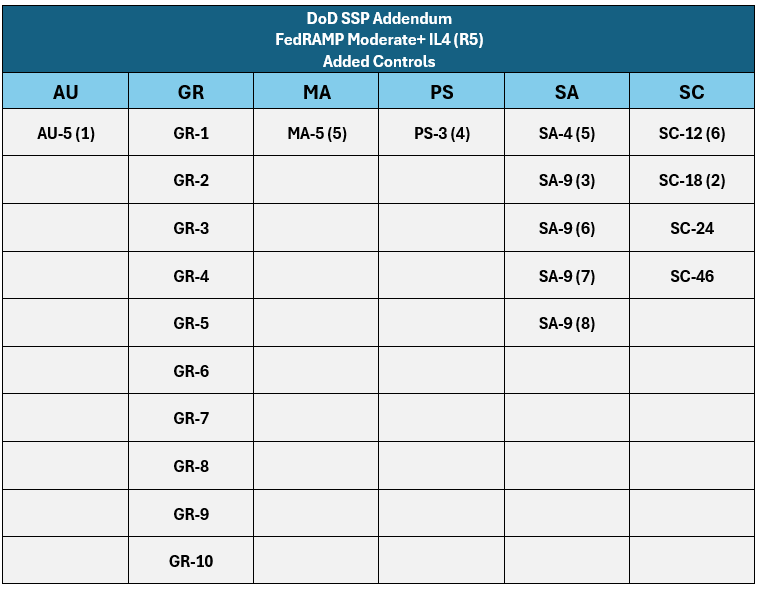
Figure 5. FedRAMP Moderate+ IL5 Revision 5 Added Controls.
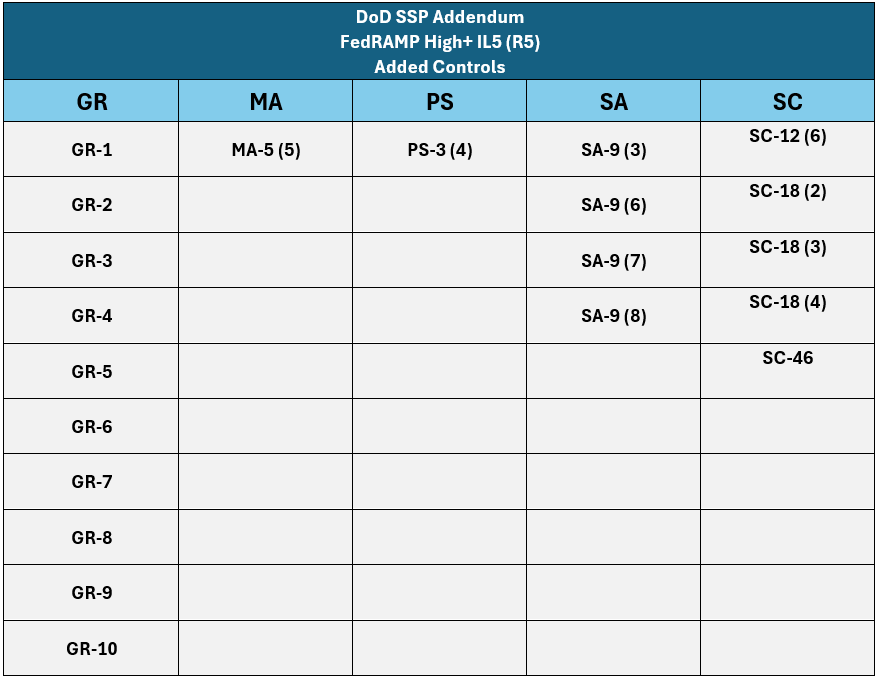
Figure 6. FedRAMP High+ IL5 Revision 5 Added Controls.
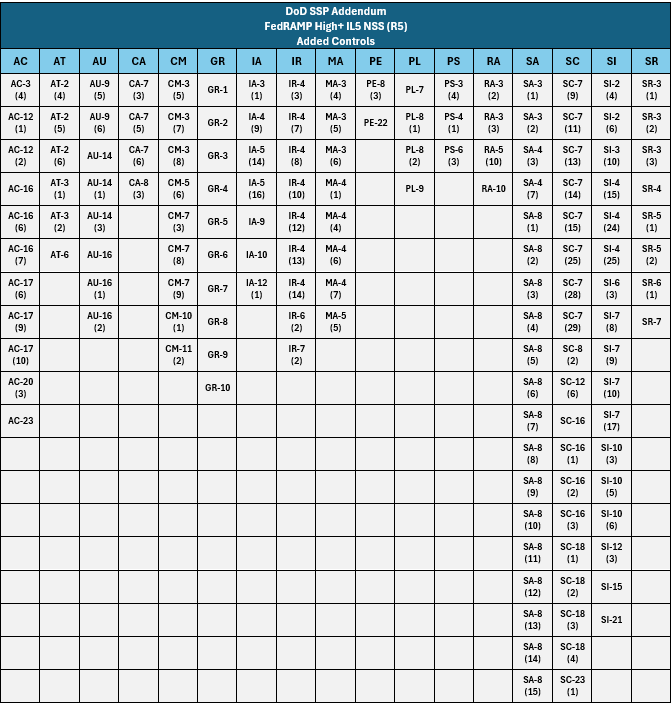
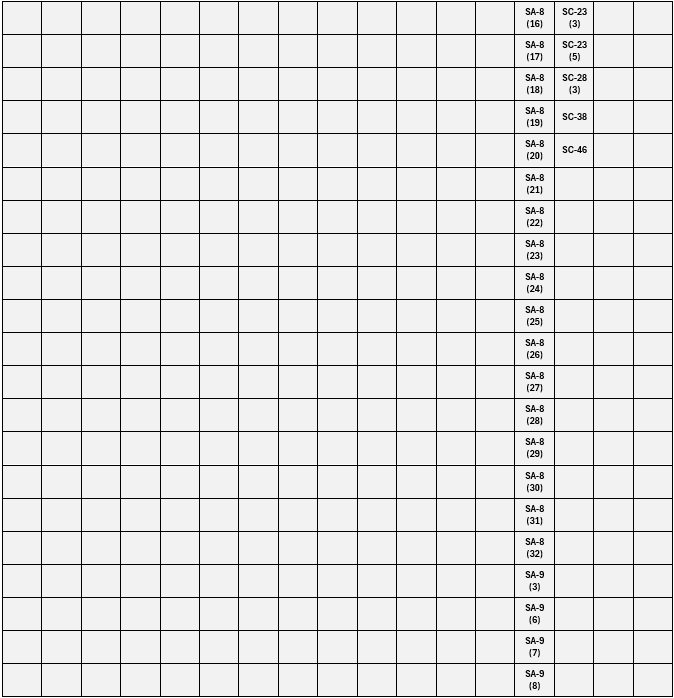
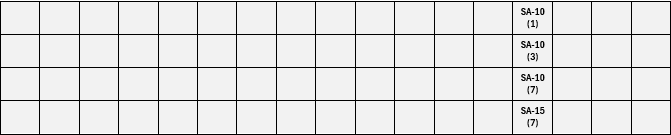
Figure 7. FedRAMP High+ IL5 NSS Revision 5 Added Controls.
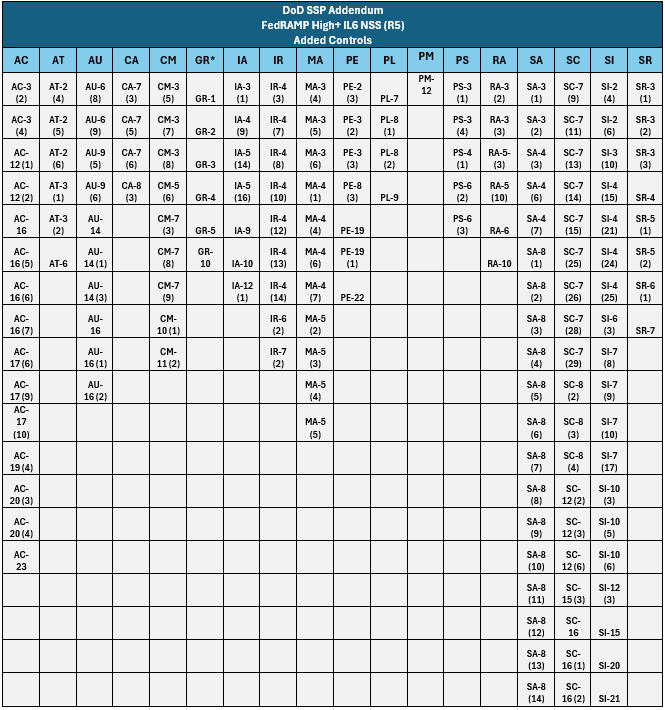
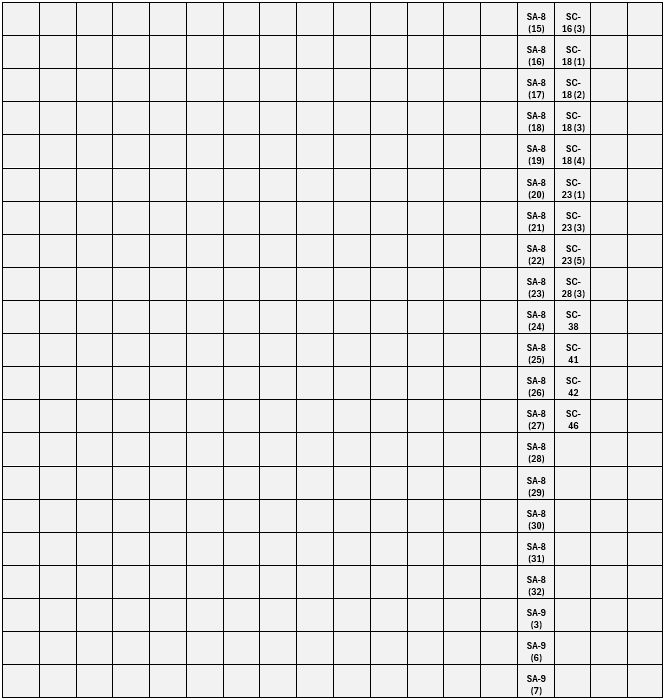
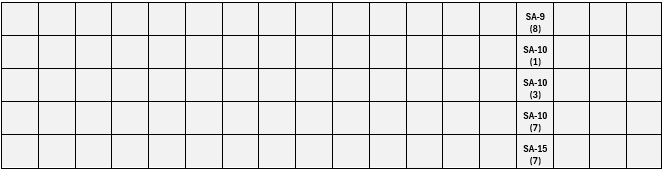
Figure 8. FedRAMP High+ IL6 NSS Revision 5 Added Controls.
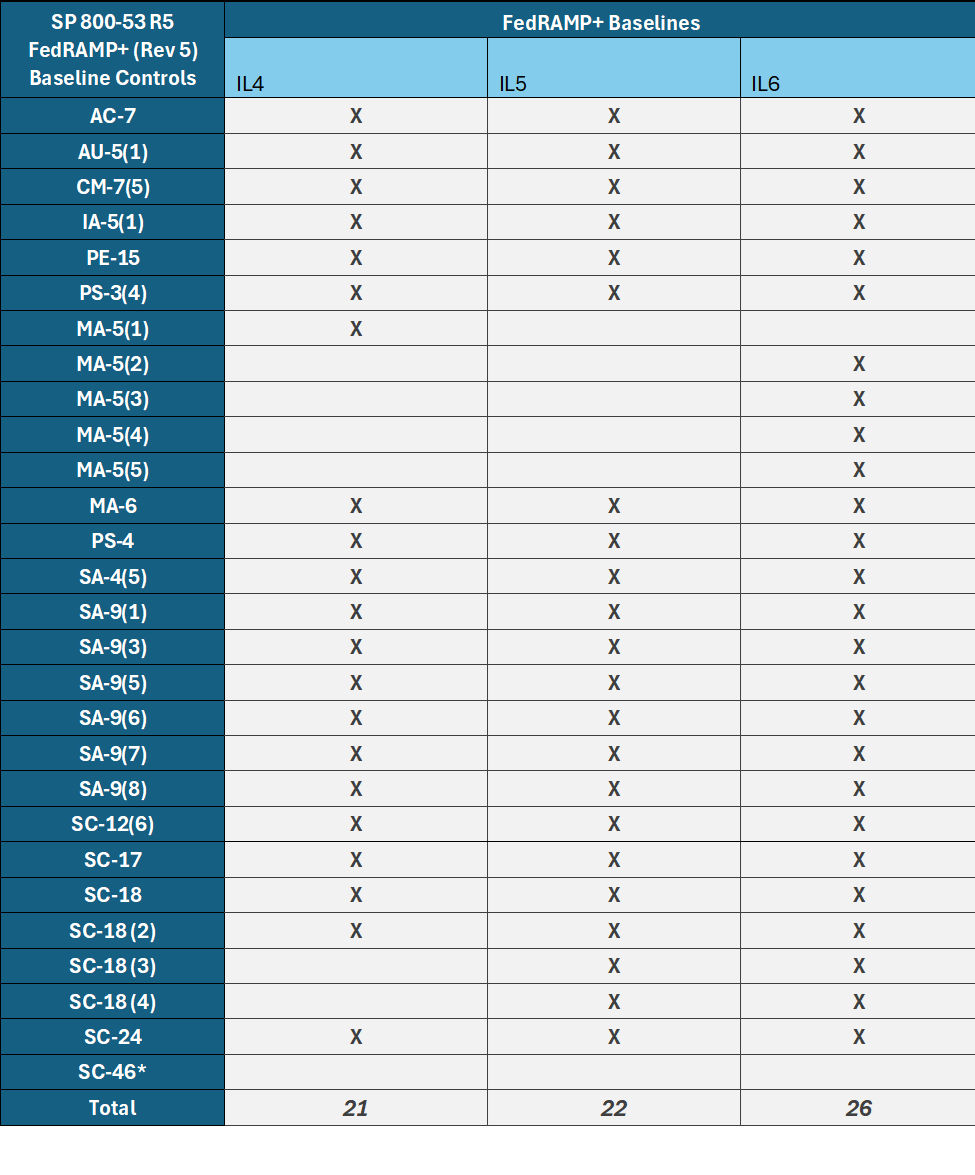
Figure 9. FedRAMP+ Rev 5 Controls from DoD CSP SRG.
*SC-46 only in scope if DISA Cross-Domain Enterprise Service (CDS/CDES) is leveraged.
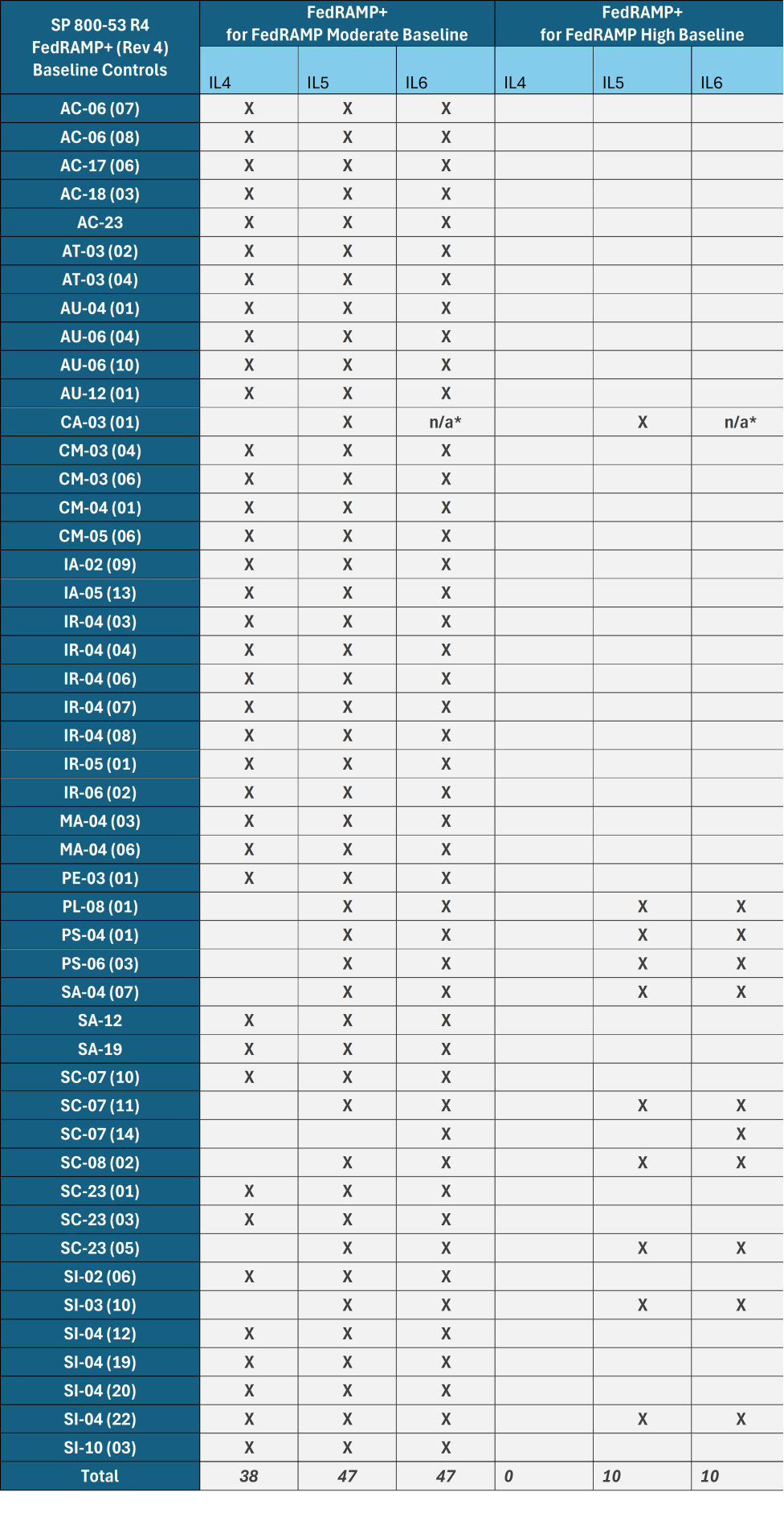
Figure 10. FedRAMP+ Rev 4 Controls.
*Most IL5 FedRAMP+ C/CEs are also applicable at IL6. The use of n/a for IL6 for CA-03 (01) is because the CE addresses "Unclassified National Security System Connections" and is therefore not selectable or applicable for Classified NSS.
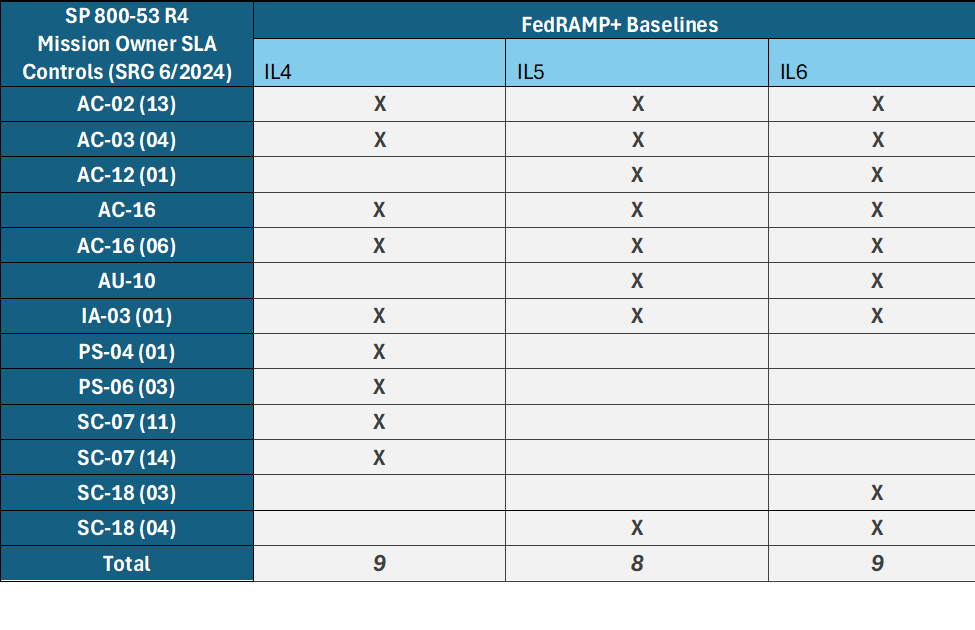
Figure 11. FedRAMP+ Mission Owner SLA Controls (Latest SRG 6/2024).
References
https://dl.dod.cyber.mil/wp-content/uploads/stigs/zip/U_Cloud_Computing_Y24M07_SRG.zip
https://dl.dod.cyber.mil/wp-content/uploads/cloud/pdf/unclass-dod_cloud_authorization_process.pdf


