DFARS | CMMC - What You Need to Know as a Contractor
CMMC Overview
The purpose of the new Cybersecurity Maturity Model Certification (CMMC) is to measure the level of cybersecurity maturity of prime contractors and their supply chain that work with the Department of Defense (DoD) to protect Controlled Unclassified Information (CUI). CMMC encompasses the security requirements for CUI specified in NIST SP 800-171 for DFARS Clause 252.204-7012 as well as the basic safeguarding requirements for federal contract information (FCI) specified in FAR Clause 52.204-21.
Controlled Unclassified Information (CUI) - is information that requires safeguarding or dissemination controls pursuant to and consistent with laws, regulations and government-wide policies, excluding information classified under Executive Order 13526 or under the Atomic Energy Act of 1954.
Federal Contract Information (FCI) - is information provided by or generated for the government under contract and not intended for public release.CMMC Level 1 focuses on information like this.
CMMC Key Points:
- CMMC is an advanced Cybersecurity framework for the entire Defense Industry.
- CMMC is more formal and structured than NIST 800-171
- Lower-level (1 and 2) requirements should be less demanding than NIST 800-171 and are more suited for smaller vendors who do not handle CUI information.
- Level 2 handles 9 CUI related practices and by itself would not be enough to cover all the requirements of NIST 800-171 and in DFARS.
- Additional clarification from the DoD will clear this up.
- CMMC contains Maturity Processes and Practices for various maturity levels.
- CMMC requirements are expected to appear in RFPs in September of 2020.
- CMMC compliance expenses are “allowable cost” that may be included in DoD contract bids.
- As an example, there is a SOCOM SBIR (a phase one SBIR) out with technical and business assistance funding specifically called out where they are going to be allowing $6,500 in value over and above the value of the SBIR specifically toward CMMC level one compliance.
- CMMC applies to future contracts and renewals only. Contracts will not be affected retroactively.
- If a single contract is in place and no planning has happened to pursue any additional contracts, then do not worry about a CMMC certification until it is time for a renewal of the contract.
-
Certifications from C3PAO audits are going to be good for three years.
Accreditation & Certification details
The accreditation process is still being finalized, however CMMC 1.0 provides useful guidance for the CMMC Accreditation Body to finalize requirements for auditors and for companies that need to start preparing for their CMMC accreditation. A key driver for contractors is that all practices for the required CMMC level must be met before accreditation will occur and accreditation must occur before contracts will be eligible to be awarded. Now is the time to train on the accreditation process and ensure that your organization is ready when accreditation occurs.
DFARS and CMMC
DFARS, the Defense Acquisition Federal Regulation Supplement, mandates that private DoD contractors adopt cybersecurity standards that follow the NIST SP 800-171 cybersecurity framework. This is the government’s effort to protect the U.S. defense supply chain. Since the DFARS mandate was released, contractors (including prime contractors and their subcontractors) have been trying to understand and implement these standards.
Due to the slow adoption of the NIST 800-171 and/or DFARS standards, the DoD has released CMMC to ensure the standards are being properly assessed and are adequate for their requirements. DFARS lets you “self-attest” to your contract requirements after you have already won the contract. CMMC makes you prove it before you can win the contract. Getting Security right for the defense industrial base is critical for all parties involved.
CMMC will not replace DFARS requirements. If you are going to a cloud environment to meet DFARS requirements, you must be FedRAMP Moderate or FedRAMP Moderate equivalent, you must also meet paragraph C through G for forensic information and incident response then you will have the requirements to do a 72-hour reporting after a breach for notification to DIBNET. Note that going for level 3, you must have 800-171 requirements with 20 additional practices and 52 maturity processes need to be in place.
100% Adherence is Required to Win Contracts
The DoD will require certified Third-Party Assessment Organizations (C3PAO) to conduct audits on all DoD contractors. The results of this audit must have 100% adherence to a contract required level of maturity for the contractor to be certified, and therefore eligible to win contracts with a given maturity rating.
One important change made from the CMMC 0.7 to the CMMC 1.0 is that you would have to have the CMMC C3PAO audit complete with the certification prior to submitting your RFP. The CMMC Working Group modified this to now say the CMMC level will be identified in the RFI or RFP you do not have to actually submit your certification until the contract is awarded.
CMMC levels and Requirements
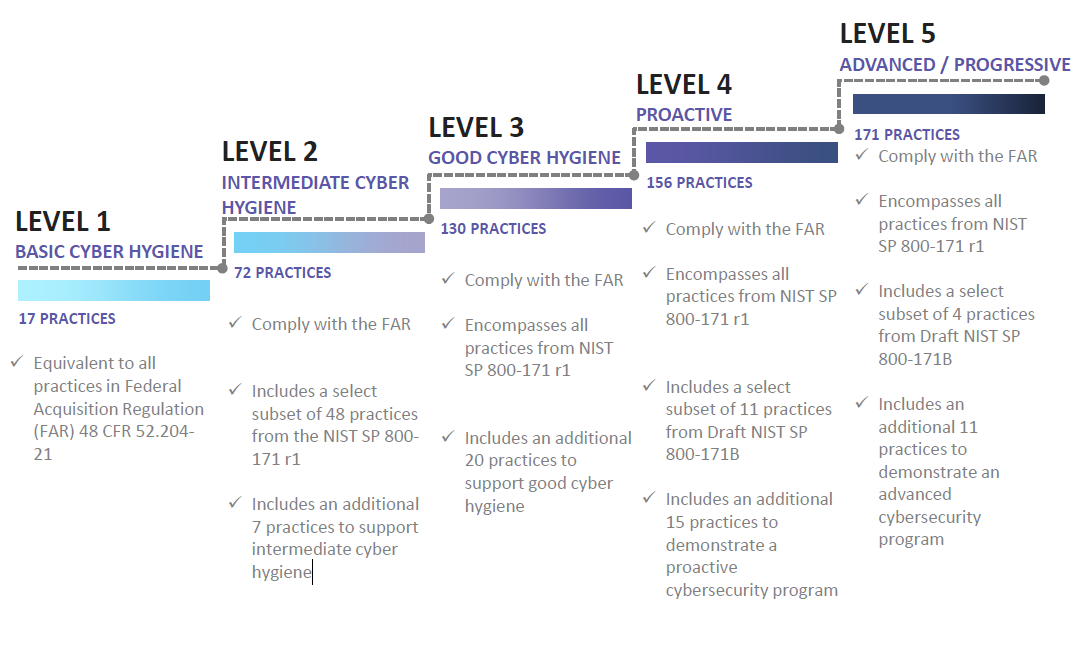
Level 1 - Basic Cyber Hygiene
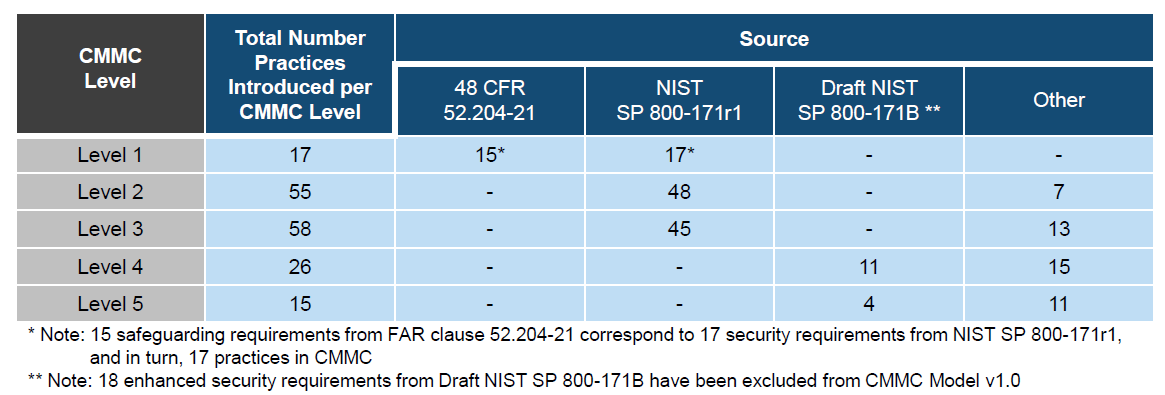
Basic safeguarding of FCI - In order to pass an audit for this level, the DoD contractor will need to implement 17 controls of NIST 800-171 rev1.
Level 2 - Intermediate Cyber Hygiene
Transition step to protect CUI - In order to pass an audit for this level, the DoD contractor will need to implement another 48 controls of NIST 800-171 rev1 plus 7 new “Other” controls. Establish policy levels and then document the practices to implement that policy.
Level 3 - Good Cyber Hygiene
Protecting CUI - In order to pass an audit for this level, the DoD contractor will need to implement the final 45 controls of NIST 800-171 rev1 plus 14 new “Other” controls. Establish, maintain and resource a plan for that [DOMAIN].
Level 4 – Proactive
In order to pass an audit for this level, the DoD contractor will need to implement 13 controls of NIST 800-171B plus 13 new “Other” controls. Review and measure [DOMAIN] activities for effectiveness.
Level 5 - Advanced / Progressive
requires extensive skills to repel advanced persistent threats (APTs). Process implementation MUST be standardized across the entire organizations. Standardize and optimize a documented approach for the [DOMAIN] across all applicable organizational units
*NOTE – Each level in CMMC requires complete adherence to preceding levels. For example, a level 3 needs to fulfill the practices of levels 1, 2, and 3.
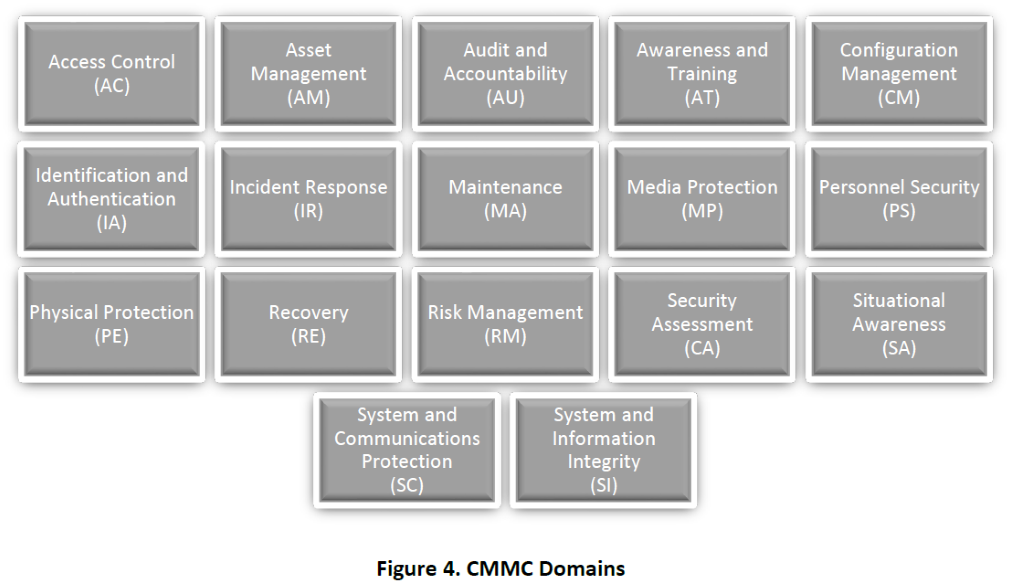
CMMC Domains are laid out here
Special Note for CMMC Level 3
Significant technical items will need attention due to the additional practices under CMMC level 3 - security information event management (SIEM), backup and restore, DNS filtering, isolating unsupported platforms, secure management protocols for managing network devices, and your spam and email protections.
Those are going be the key areas from a technical standpoint that need focusing on to move from a NIST 800-171 compliance stance to a CMMC level 3 compliance stance.
NIST 800-171 to CMMC GAPS
These are just a few additional key items that contractors consistently seem to implement weakly or not implement at all -
-
Change management is almost non-existent and in most companies.
-
Especially when you talk about change logs and true baseline configurations of an environment (Operating Systems for example).
-
CUI data flow diagrams.
-
Where CUI exists in your environment and how CUI moves through your organization.
-
Risk management and mitigation plans.
-
Audit logging and retention, especially utilizing a centralized SIEM based solution.
-
Blacklisting and whitelisting of software is not happening in most companies.
-
Especially smaller companies that have limited IT budgets and staffing.
-
Configurations and management of user installed software.
-
Most companies are trying to first secure the server locations (on-premise and/or the cloud) that have controlled unclassified information.
-
But the user workstations haven't necessarily been configured at this point.
Those are just some things to pay attention to as you're looking at continuing your track toward NIST 800-171 compliance.
CMMC Framework
The framework further divides the practices into 17 domains, with most practices contained in six domains: Access Control, Audit and Accountability, Incident Response, Risk Management, Systems and Communications Protection, and System and Information Integrity. The remaining 11 domains have most of their practices required for higher levels of certification.
As stated by Gordon Bitko (2020), a senior vice president of policy for the public sector at ITI and former CIO at FBI:
“If you are a vendor providing FedRAMP services, you are doing more than CMMC requires because FedRAMP requires continuous monitoring. That’s a real significant step forward in cybersecurity. That’s a great best practice we should be looking to work with DoD to include in the future versions of the CMMC. If you are 3, 4 or 5 steps down, it is an open question for you now. Can you leverage those processes through FedRAMP-approved services? You have to figure that out yourself. There are lots of people asking those questions now” (Bitko, G. 2020).
CMMC Full Implementation
Timeline for full rollout is by 2026. This allows time for existing contracts to be completed and companies to prepare for their requirements. Companies need to be proactive in assessing where they are and where they need to be.
For 2020 Katie Arrington said (Ellen Lord as well) that the CMMC working group expects that they'll have 10 contracts with a total of 150 companies per contract in 2020 released. That's a total of 1,500 companies that will have to have the CMMC certifications complete in the calendar year 2020. Now that's a relatively small number, but that's probably going to be some of your most active companies that are in the DIB. So, CMMC is going to make an impact in 2020.
Some the focus of the contracts for these ten are going be things like nuclear, missile defense contracts, OTAs, SBIRs, and STRs.
Cited Source:
Government Matters, (2020). New CMMC standards issued, Retrieved from https://govmatters.tv/new-cmmc-standards-issued/


