Automatically Generating SBOMs for Customers
Software bills of materials (SBOMs) are one of the hottest topics in cybersecurity. An SBOM contains information about all of the software components of a computing product or service. An SBOM gives a customer visibility into the composition of software and services, which enables them to be aware at all times of all known vulnerabilities, supply chain compromises, and other cybersecurity issues potentially affecting them.
Many federal agencies are already requiring their CSPs and other vendors to provide them with SBOMs. As we discussed in our previous blog post, Executive Order (EO) 14028 and OMB Memorandum M-22-18 require software producers with federal agency customers to retain artifacts of their secure software development processes and to share certain artifacts with their federal customers. SBOMs are a form of artifact that many federal agencies are requesting.
It’s important for CSPs to understand federal agencies’ SBOM requirements and expectations. The content and formats of SBOMs are rapidly evolving, and the federal government has already issued several sets of requirements, with more likely on the way. In this blog post, we’ll get you up to speed on the latest SBOM developments, and we’ll provide you with advice on how to integrate automated SBOM production into your existing technologies. The goal is to have one process that generates SBOMs which will meet the needs of all your customers.
SBOM Composition and Generation
In support of EO 14028, the Department of Commerce defined the minimum elements that every SBOM must contain. These elements include basic data fields such as the name and version number for each software component, and information on dependencies that each software component may have on other software components, as well as the identity of the SBOM’s author and a timestamp for when the SBOM was created.
However, this same document goes further than just listing data fields. It also discusses available data formats for generating SBOMs—Software Package Data eXchange (SPDX), CycloneDX, and Software Identification (SWID) tags—and it requires that all SBOMs provided to federal agencies must use one of these formats.
Most importantly, the Department of Commerce document specifies requirements and recommendations for the practices and processes for generating, distributing, and maintaining SBOMs. Examples of these include the following:
- Generate and issue a new SBOM every time a software component is updated or a software component from a dependency is updated
- Generate and issue a new SBOM when an error is found in an existing SBOM
- Include all software components and first-order software component dependencies in SBOMs
- Explicitly indicate all instances where dependencies are not fully known
- Make a new SBOM available and accessible quickly by all parties who need it, and provide advertisement and/or discovery mechanisms so all parties know of the new SBOM’s availability
The result of these requirements and recommendations is that CSPs may need to regenerate SBOMs and distribute them to their customers numerous times every day.
Leveraging AWS Capabilities for SBOMs
AWS recently added capabilities to Amazon Inspector for automatically generating SBOMs for all the software components that Amazon Inspector is monitoring. The screenshot shows the Inspector interface for SBOM management. Inspector can export the SBOMs it creates in either CycloneDX or SPDX format, both of which satisfy federal agency requirements. The “Findings” feature offers filtering capabilities for generating SBOMs for particular subsets of software components, such as container images with a particular tag.
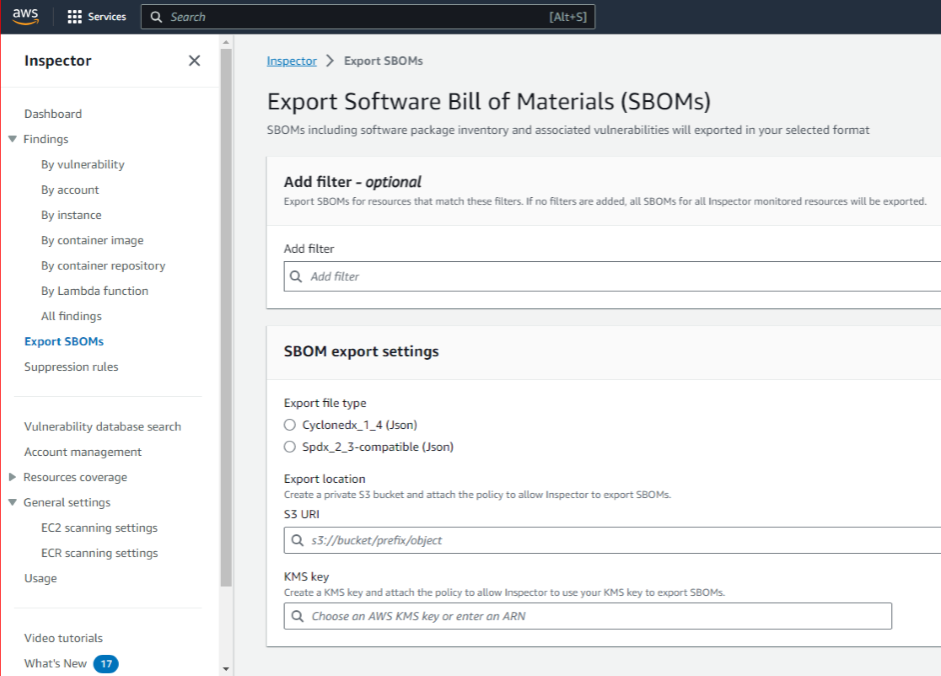
Amazon Inspector can automate the SBOM generation process to help comply with federal agency requirements. In addition, each CSP must decide how to make their SBOMs accessible to customers and how to notify affected customers of an update or correction in an SBOM, then implement, maintain, and monitor the necessary solutions. These decisions can be difficult—for example, whether to make SBOMs publicly available, which simplifies distribution but reveals information about vulnerabilities to attackers, or to restrict access to SBOMs, which necessitates implementing access control solutions for SBOMs. Regardless of the access method, CSPs must also provide an advertisement or discovery mechanism so their customers are immediately informed of any SBOM updates.
Consultants can aid CSPs in understanding the latest SBOM requirements from federal agencies and in leveraging AWS’s capabilities for implementing all the SBOM automation needed to effectively and efficiently generate new SBOMs in compliance with federal requirements. Another area where consultants can be particularly helpful is in designing and implementing SBOM advertisement or discovery mechanisms for CSP customers that comply with federal requirements.
If you have any questions or need assistance in implementing your SBOM automation, contact us at info@infusionpoints.com!
References
AWS announces Software Bill of Materials export capability in Amazon Inspector
Software Bill of Materials (SBoM)
Software Security in Supply Chains
The Minimum Elements For a Software Bill of Materials (SBOM)


